Our Application Penetration Testing service helps businesses to identify and remediate security vulnerabilities in Web, API, and Mobile applications before attackers can exploit them.
We find weaknesses and provide clear recommendations on how to protect your business.
While each member of our expert team is a certified specialist with extensive experience, we believe in following a strong, clear and structured approach which makes our services stand out among others. What we follow includes but not limited to the below principles:
With over 250 distinct manual tests, our approach goes far beyond simple automated scanners.

We adhere to the latest OWASP testing guidelines as our baseline, including WSTG, MSTG, and more, ensuring a robust and comprehensive testing approach.

We help you achieve compliance with industry security standards such as ISO 27001, PCI-DSS, and NIST through our high-standard Pentesting methodology and execution.
Each report includes an executive summary, detailed findings, risk assessment, impact analysis, and clear remediation recommendations, all presented in a professional, concise, and actionable format—regardless of system size or company.
We provide guidance on fixing vulnerabilities and follow-up testing to confirm resolution. A free retest is included for up to one year.

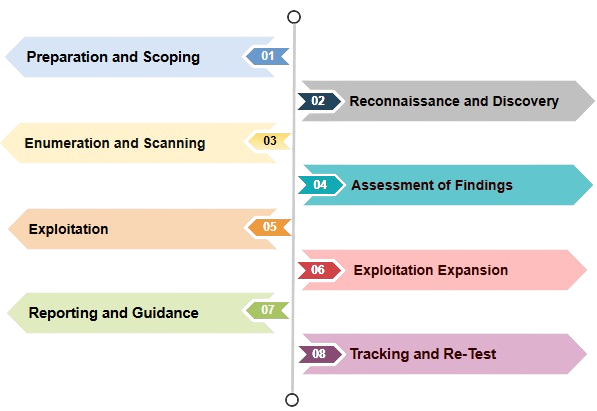
Our experts at CyberPen have developed and adhere to the following methodology, inspired by industry-recognized frameworks such as OWASP (for applications), OSSTMM (for networks), and PTES. This structured approach ensures that penetration testing is conducted without bias or subjective influence, maintaining objectivity throughout the process.
Adhering to a well-defined methodology ensures comprehensive testing, leaving no critical areas overlooked. This disciplined approach allows us to measure security improvements effectively and make informed decisions to strengthen your security posture.
A comprehensive pentest report is crucial for identifying vulnerabilities and mitigating risks. Ours includes the essentials, providing clear guidelines and actionable insights for better security.
Overview of test objectives, key findings, business impact, and critical recommendations
Descriptions of vulnerabilities, evidence, risk ratings, and affected systems.
Evaluation of each vulnerability’s likelihood, impact, and priority.
Actionable steps to fix vulnerabilities, including mitigation strategies.
Mapping of findings to relevant compliance frameworks and remediation steps.
Summary of findings, final recommendations, and acknowledgements.
Technical details, test methodology, tools used, and network diagrams.
Post-test consultation and expert guidance are available to assist with remediation, with a free retest offered for up to one year.
Organizations that develop, use, or rely on web and mobile applications need application or mobile penetration testing to ensure security and compliance. This includes:
If an application collects, processes, stores, or transmits sensitive data, it needs security testing to prevent breaches.
CyberPen.IO proactively identifies your vulnerabilities and provides expert recommendations to secure your system
Copyright © 2025 All rights reserved.