Our Vulnerability Management Service provides continuous monitoring, actionable insights, and expert guidance across your internal/external network, applications, and APIs. As a cost-effective complement to penetration testing, it ensures ongoing protection by identifying and prioritizing vulnerabilities in real-time, reducing risks between pentest engagements.
Our Vulnerability Management service combines advanced tools, expert insights, and a structured approach to keep your systems secure. Here’s what makes us different:
We use automated scans paired with manual validation to uncover even the most hidden vulnerabilities, ensuring no critical weakness is overlooked.

We prioritize vulnerabilities based on exploitability, impact, and your business context, helping you focus on what matters most.

Our assessments align with standards like ISO 27001, NIST, and PCI-DSS, ensuring compliance while boosting your security posture.
Our reports provide clear, concise insights, including risk ratings, impact analysis, and step-by-step remediation guidance.
We offer ongoing monitoring, remediation assistance, and validation to ensure vulnerabilities are resolved and stay resolved.

At CyberPen, we follow a structured Vulnerability Management (VM) methodology, inspired by NIST 800-40, ISO 27001, and CVSS for risk prioritization. This ensures a systematic, objective, and continuous process for identifying, assessing, prioritizing, and remediating security vulnerabilities across your IT infrastructure.
Our methodology includes:
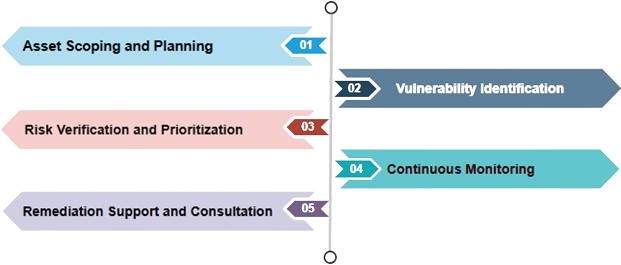
This structured, risk driven approach ensures comprehensive coverage of your networks, applications, and APIs, with continuous monitoring to proactively address emerging threats. We deliver actionable insights through risk-based prioritization and remediation guidance, while aligning with industry standards to keep your business compliance-ready.
Organizations that rely on IT infrastructure, networks, and digital assets—including applications and APIs (DAST)—need continuous vulnerability management to maintain security and compliance. This includes:
With evolving threats, a proactive vulnerability management program is essential to detect and remediate security weaknesses before exploitation.
CyberPen.IO proactively identifies your vulnerabilities and provides expert recommendations to secure your system
Copyright © 2025 All rights reserved.